公私钥、数字签名、数字证书
Alice,信息发送方;Bob,信息接收方。
Q:如何保证信息传输过程中,其他人看不到?
公私钥
加解密分为对称加密和非对称加密
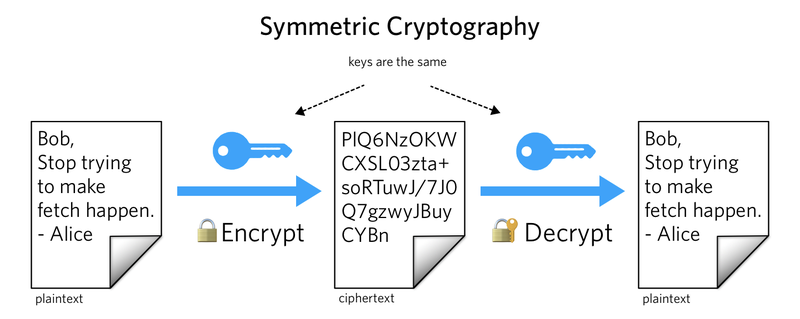
对称加密:加解密用到的密钥是一样的。密钥泄露风险较大
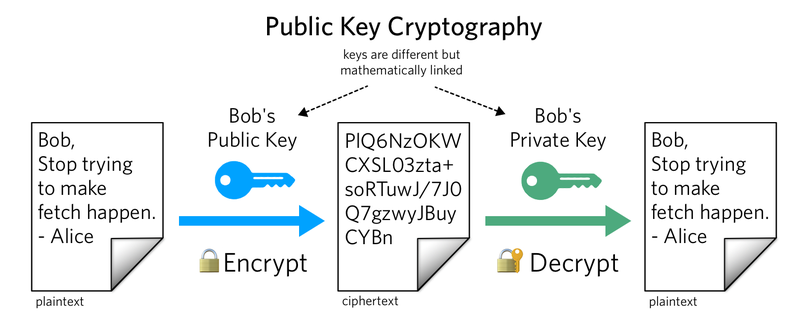
非对称加密:加解密用到的密钥是不一样的,密钥是一对。公钥对外公开,私钥保密。
公私钥用来对信息进行加解密,解决信息明文传输问题。
可以通过公钥加密,然后通过私钥解密。公钥通常用来加密
可以通过私钥加密,然后通过公钥解密。私钥通常用来签名
加解密过程:
# 生成私钥
# openssl genpkey -algorithm RSA -outform PEM -out private_key.pem
.............................++++++
................++++++
# 根据私钥生成对应的公钥
# openssl rsa -in private_key.pem -outform PEM -pubout -out public_key.pem
writing RSA key
# 构造明文
# echo 'Hello world' > plain_text
# 利用公钥对明文进行加密
# openssl rsautl -encrypt -inkey public_key.pem -pubin -in plain_text -out encrypted_text
# 利用私钥对密文进行解密
# openssl rsautl -decrypt -inkey private_key.pem -in encrypted_text -out decrypted_text
# cat decrypted_text
Hello world
Q:如何保证信息确实是Alice发出的,而不是其他人伪造的?
数字签名
数字签名用来表明信息归属,解决信息归属问题。
用Alice的公钥解密能获取到的信息,表明该信息确实属于Alice
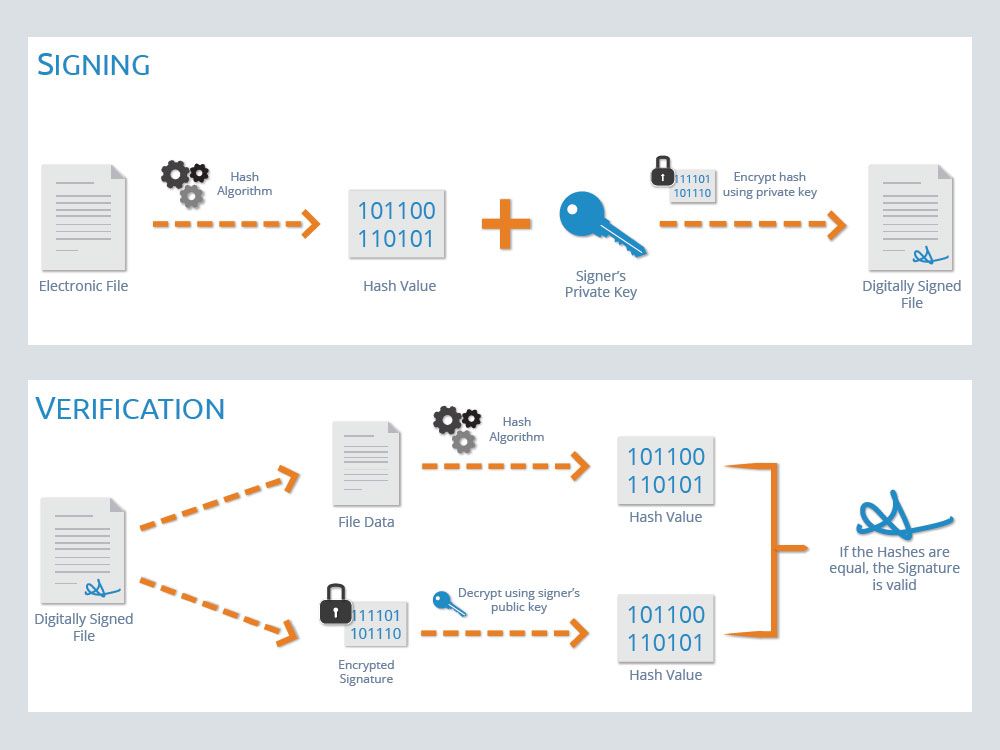
Alice签名:1、对信息进行Hash运算;2、对Hash值采用私钥进行加密,最后生成签名文件
Bod验签:1、拿到信息和对应的签名文件;2、对信息进行Hash运算;3、采用Alice的公钥解密签名文件;4、比对Hash值,一致则验证通过
Hash运算:1、唯一性,无法找到产生相同输出的输入;2、单向性,法通过输出反推出输入。
Q:如何保证获取到的公钥是Alice的,而不是其他人恶意发布的?
数字证书
数字证书用来说明证书拥有者的真实身份信息,解决证书属主问题
证书=公钥+个人/组织信息(姓名+地址+电子邮件+公司等)
X.509证书关键内容:
- Issuer: 证书颁发机构
- Subject: 证书拥有者
- Subject Public Key Info: 证书拥有者的公钥
- Signature Algorithm: 签名算法及数字签名
Q:如何保证Alice的证书是可信的?
A:CA机构,通过第三方权威机构做信用背书,解决共识问题
- Alice用自己的公钥和个人信息向CA机构发送证书申请CSR
- CA验证Alice身份,使用CSR身份信息生成证书,并采用根私钥对证书进行签名
- Bob使用CA机构的公钥对Alice的证书进行验证,确认Alice的公钥及其身份
CA的公钥通常预置在操作系统中
Q:如何保证CA的私钥未被泄露?
A:证书链,通过增加中间证书,降低泄露影响面

示例
生成CA私钥和证书
# openssl req -newkey rsa:2048 -nodes -keyout rootCA.key -x509 -days 365 -out rootCA.crt
Generating a 2048 bit RSA private key
...........................+++
..................................+++
writing new private key to 'rootCA.key'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:Shaanxi
Locality Name (eg, city) [Default City]:Xi'an
Organization Name (eg, company) [Default Company Ltd]:Test Root CA
Organizational Unit Name (eg, section) []:
Common Name (eg, your name or your server's hostname) []:Test Root CA
Email Address []:ca@test.com
# ls rootCA.key rootCA.crt
rootCA.crt rootCA.key
生成中间证书的私钥和CSR
# openssl req -new -nodes -keyout intermediate.key -out intermediate.csr
Generating a 2048 bit RSA private key
......................................................................+++
....+++
writing new private key to 'intermediate.key'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:Shaanxi
Locality Name (eg, city) [Default City]:Xi'an
Organization Name (eg, company) [Default Company Ltd]:Test Intermediate CA
Organizational Unit Name (eg, section) []:
Common Name (eg, your name or your server's hostname) []:Test Intermediate CA
Email Address []:intermediate@test.com
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
# ls intermediate.key intermediate.csr
intermediate.csr intermediate.key
根据CSR生成中间证书
# mkdir db
# touch db/index
# cat intermediateCA.conf
[ ca ]
default_ca = intermediate_ca
[ intermediate_ca ]
dir = .
private_key = $dir/rootCA.key
certificate = $dir/rootCA.crt
new_certs_dir = $dir/
serial = $dir/crt.srl
database = $dir/db/index
default_md = sha256
policy = policy_any
email_in_dn = no
[ policy_any ]
domainComponent = optional
countryName = optional
stateOrProvinceName = optional
localityName = optional
organizationName = optional
organizationalUnitName = optional
commonName = optional
emailAddress = optional
[ ca_ext ]
keyUsage = critical,keyCertSign,cRLSign
basicConstraints = critical,CA:true
subjectKeyIdentifier = hash
authorityKeyIdentifier = keyid:always
中间证书,需要设置basicConstraints包含CA:true,标明该证书属于证书机构的证书,可以用于签发和验证用户证书
# openssl ca -config intermediateCA.conf -days 365 -create_serial -in intermediate.csr -out intermediate.crt -extensions ca_ext -notext
Using configuration from intermediateCA.conf
Check that the request matches the signature
Signature ok
The Subject's Distinguished Name is as follows
countryName :PRINTABLE:'CN'
stateOrProvinceName :ASN.1 12:'Shaanxi'
localityName :ASN.1 12:'Xi'an'
organizationName :ASN.1 12:'Test Intermediate CA'
commonName :ASN.1 12:'Test Intermediate CA'
Certificate is to be certified until Jul 29 07:34:53 2023 GMT (365 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
# ls intermediate.crt
intermediate.crt
生成Alice的私钥和CSR
# openssl req -new -nodes -keyout Alice.key -out Alice.csr
Generating a 2048 bit RSA private key
.....................+++
..............................+++
writing new private key to 'Alice.key'
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:Shaanxi
Locality Name (eg, city) [Default City]:Xi'an
Organization Name (eg, company) [Default Company Ltd]:Alice Company
Organizational Unit Name (eg, section) []:
Common Name (eg, your name or your server's hostname) []:Alice
Email Address []:alice@test.com
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
# ls Alice.key Alice.csr
Alice.csr Alice.key
生成Alice的用户证书
# openssl x509 -req -in Alice.csr -CA intermediate.crt -CAkey intermediate.key -CAcreateserial -out Alice.crt
Signature ok
subject=/C=CN/ST=Shaanxi/L=Xi'an/O=Alice Company/CN=Alice/emailAddress=alice@test.com
Getting CA Private Key
# ls Alice.crt
Alice.crt
Bob对Alice的用户证书进行验证
通过指定证书进行验证:
# openssl verify -CAfile rootCA.crt -untrusted intermediate.crt Alice.crt
Alice.crt: OK
验证时需要同时指明根证书和中间证书
或者,通过证书链进行验证:
# cat rootCA.crt intermediate.crt > chain.crt
# openssl verify -CAfile chain.crt Alice.crt
Alice.crt: OK
实际使用中,根证书自身就是可信的,而且预置在OS中的,可以直接通过中间证书进行验证
参考:
- https://segmentfault.com/a/1190000024523772
- https://www.zhaohuabing.com/post/2020-03-19-pki/
